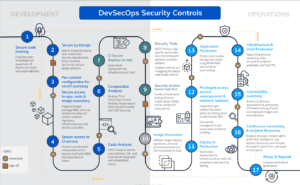
The Software Development Life Cycle (SDLC) is a critical process that ensures the successful creation and delivery of software applications. However, with the increasing complexity of software systems and the growing number of security threats, it’s essential to integrate security seamlessly into the SDLC to safeguard sensitive data and protect against potential vulnerabilities.
This is where DevOps security services come into play, providing the necessary tools and practices to enhance the security of your SDLC. In this blog, we’ll delve into the world of DevOps security services and explore how they secure your SDLC.
Understanding the SDLC
Before we dive into the role of DevOps security services, let’s briefly recap what the Software Development Life Cycle (SDLC) entails. The SDLC is a series of stages that guide the development and maintenance of software applications. These stages typically include:
Planning:
In this phase, project requirements are gathered, and a roadmap is created for the entire development process. It’s essential to identify potential security risks at this stage.
Planning is the foundational stage of the SDLC, where project stakeholders define the scope, objectives, and requirements of the software project. This phase involves activities such as:
- Requirement Gathering: Teams collect and analyze requirements from stakeholders, including business analysts, product owners, and end-users. Identifying security-related requirements is critical to understanding the security needs of the application.
- Risk Assessment: During the planning phase, it’s crucial to conduct a preliminary risk assessment. This involves identifying potential security threats and vulnerabilities that may affect the project. Risk assessment helps prioritize security measures and allocate resources effectively.
Design:
Software architects and designers create a blueprint of the application’s structure and functionality. Security considerations should be integrated into the design to prevent vulnerabilities.
The design phase focuses on translating the requirements gathered in the planning phase into a detailed technical design. Here’s a closer look at the key activities in this phase:
- Architecture Design: Software architects design the overall structure of the application, including its components, modules, and data flows. Security architects collaborate with the team to ensure that security controls are integrated into the architecture.
- Data Security Design: Designers plan how sensitive data will be handled and protected within the application. This includes data encryption, access control mechanisms, and data storage security.
- Threat Modeling: Threat modeling is a critical security activity in the design phase. Teams identify potential threats and attack vectors and design countermeasures to mitigate these risks. Threat modeling helps shape the security features of the application.
Development:
Developers write the actual code for the software. Secure coding practices should be followed to minimize the introduction of security flaws.
Development is where the actual coding of the software takes place. This phase involves writing, testing, and integrating code based on the design specifications. Secure development practices are essential to building a robust and secure application:
- Secure Coding Guidelines: Development teams should adhere to secure coding guidelines and best practices. This includes input validation, output encoding, and secure error handling to prevent common vulnerabilities like SQL injection, cross-site scripting (XSS), and buffer overflows.
- Code Reviews: Regular code reviews by peers and security experts can help identify and address security issues early in the development process. Code reviews should focus on security-related code patterns and vulnerabilities.
- Static Code Analysis: Static code analysis tools scan the source code for potential security vulnerabilities. These tools can identify issues such as insecure coding practices, code smells, and potential vulnerabilities.
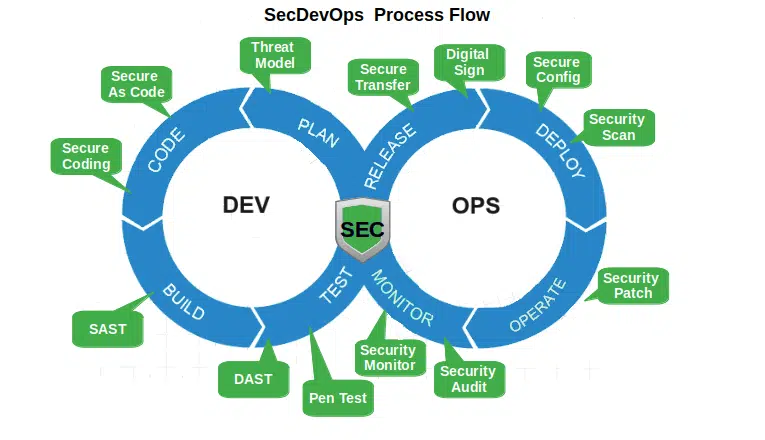
Testing:
Various types of testing, including functional, integration, and security testing, are performed to identify and rectify issues. Security testing is especially crucial for vulnerability detection.
Testing is a critical phase in the SDLC where the application’s functionality and security are evaluated. Let’s explore the various testing activities and their significance in more detail:
- Functional Testing: Functional testing ensures that the application’s features and functionality work as intended. Test cases are designed to validate that the software meets the specified requirements.
- Integration Testing: Integration testing assesses how different components of the application work together. It verifies that data flows correctly between modules and identifies integration issues.
- Security Testing: Security testing focuses on identifying vulnerabilities and weaknesses in the application’s security posture. This includes:
- Penetration Testing: Ethical hackers (penetration testers) attempt to exploit vulnerabilities in the application to uncover potential security risks. They simulate real-world attacks to assess the application’s resilience.
- Vulnerability Scanning: Automated tools scan the application for known vulnerabilities, such as outdated libraries or misconfigurations. These tools provide a quick way to identify and remediate common security issues.
- Code Review: Security experts conduct a thorough review of the codebase to identify security-related coding mistakes and vulnerabilities.
- Performance Testing: Performance testing assesses how the application performs under various conditions, such as high user loads or concurrent requests. While not directly focused on security, performance issues can indirectly lead to security vulnerabilities.
Deployment:
The software is deployed to production environments, and continuous monitoring begins to detect any security incidents promptly.
Deployment marks the transition from development to production, where the application is made available to users. Security considerations during this phase include:
- Secure Deployment Practices: Secure deployment practices involve ensuring that the application is configured securely in the production environment. This includes secure server configurations, network security settings, and access controls.
- Continuous Monitoring: After deployment, continuous monitoring of the application is crucial. Security teams use monitoring tools to detect and respond to security incidents in real-time. This includes monitoring for abnormal activities, intrusion attempts, and system vulnerabilities.
- Incident Response Planning: Organizations should have an incident response plan in place to address security breaches or incidents swiftly and effectively. The plan outlines the steps to take when a security incident is detected.
Maintenance:
Ongoing maintenance and updates are carried out to ensure the software remains secure and functional.
Maintenance is the final phase of the SDLC, where the application is regularly updated, patched, and improved. Security-related activities during this phase include:
- Patch Management: Regularly applying security patches and updates to the application and its dependencies is crucial to address known vulnerabilities.
- Security Updates: As new security threats emerge, security teams must assess and implement updates to protect the application from evolving risks.
- Code Maintenance: Developers may continue to work on the application to add new features or make enhancements. It’s essential to maintain secure coding practices during these updates to avoid introducing new vulnerabilities.
The Need for DevOps Security Services
In the past, security was often considered a separate phase of the SDLC, leading to a multitude of challenges. DevOps, which emphasizes collaboration and automation, has revolutionized software development, allowing for faster and more efficient releases. However, this increased speed can sometimes compromise security. DevOps security services bridge this gap by integrating security seamlessly into the development pipeline. Here’s how they do it:
Early Security Assessment
DevOps security services emphasize early security assessment, starting from the planning and design phases of the SDLC. By identifying potential security risks and vulnerabilities early on, teams can address them proactively, reducing the chances of security incidents later in the development process.
Early security assessment involves:
- Threat Modeling: Identifying potential threats and attack vectors during the design phase and devising strategies to mitigate them.
- Security Requirements Definition: Defining security requirements that align with the overall project objectives and compliance standards.
- Security Testing Automation: Integrating automated security testing tools into the CI/CD pipeline to continuously assess code for vulnerabilities.
Automation of Security Tests
One of the key principles of DevOps is automation. DevOps security services leverage automation tools to conduct security tests continuously throughout the development cycle. This includes static code analysis, dynamic application security testing (DAST), and container security scans. Automated security testing ensures that vulnerabilities are detected and remedied promptly.
Automation of security tests involves:
Static Code Analysis: Automated tools analyze the source code for security vulnerabilities without executing it. They can identify issues such as code injection vulnerabilities, insecure authentication mechanisms, and data leakage risks.
- Dynamic Application Security Testing (DAST): DAST tools simulate attacks on a running application to discover vulnerabilities like SQL injection, cross-site scripting (XSS), and authentication weaknesses.
- Container Security Scanning: For applications deployed in containers, security scanning tools assess container images for vulnerabilities and misconfigurations.
Continuous Integration and Continuous Deployment (CI/CD) Security
CI/CD pipelines are the heart of DevOps, enabling rapid and frequent code deployments. DevOps security services integrate security checks into these pipelines, ensuring that no insecure code makes its way into production. Automated security gates can halt the deployment process if vulnerabilities are detected, providing an additional layer of protection.
CI/CD security involves:
- Pipeline Orchestration: Designing CI/CD pipelines that include security gates and checks at critical stages, such as code commit, build, and deployment.
- Policy Enforcement: Defining and enforcing security policies within the CI/CD process, ensuring that code adheres to security standards and best practices.
- Automated Remediation: Implementing automated remediation processes to address security findings quickly and efficiently.
Threat Intelligence Integration
DevOps security services also incorporate threat intelligence feeds and databases. This allows teams to stay updated on the latest security threats and vulnerabilities. By leveraging threat intelligence, organizations can proactively protect their applications from emerging risks.
Threat intelligence integration involves:
- Data Collection: Collecting and aggregating data from various threat intelligence sources, including security bulletins, vulnerability databases, and industry reports.
- Analysis: Analyzing the collected data to identify relevant threats and vulnerabilities that may impact the organization.
- Integration with Security Tools: Feeding threat intelligence data into security tools and systems to enhance threat detection and response capabilities.
- Threat Hunting: Proactively searching for signs of advanced threats and potential risks within the organization’s infrastructure and applications.
Secure Configuration Management
Configuration management is a vital aspect of securing applications. DevOps security services help organizations define and maintain secure configurations for their infrastructure and application components. This reduces the attack surface and minimizes the risk of misconfigured systems.
Secure configuration management involves:
- Configuration Baselines: Establishing a secure baseline for system and application configurations. This includes hardening server settings, network configurations, and access controls.
- Change Control: Implementing change management processes to track and approve changes to configurations. Unauthorized changes can introduce vulnerabilities.
- Continuous Monitoring: Continuously monitoring configurations to detect and remediate drift from the established secure baseline.
External References and Further Reading
For more in-depth information on DevOps security services and best practices, you can explore the following external references:
ISmile DevSecOps: Top 10 Best Practices
NIST Special Publication 800-183: Cybersecurity Practice Guide, “DevSecOps”
Conclusion
DevOps security services play a crucial role in securing the Software Development Life Cycle. By integrating security into every phase of the SDLC and leveraging automation and threat intelligence, organizations can develop and deploy software applications with greater confidence.
With the ever-evolving threat landscape, embracing DevOps security services is not just a best practice; it’s a necessity to protect your software assets and data from potential breaches and vulnerabilities.
So, consider implementing DevOps security services in your organization to ensure the security and integrity of your software applications.